Mailing List
Sign Up and Get Our Best Content First
Each week we send 1 email to smart Drupal website owners. Enter your email below to receive our updates.
We will not share your email. 100% Privacy
Update: This is fixed in Drupal 7.56 - update your sites!
To resolve this issue:
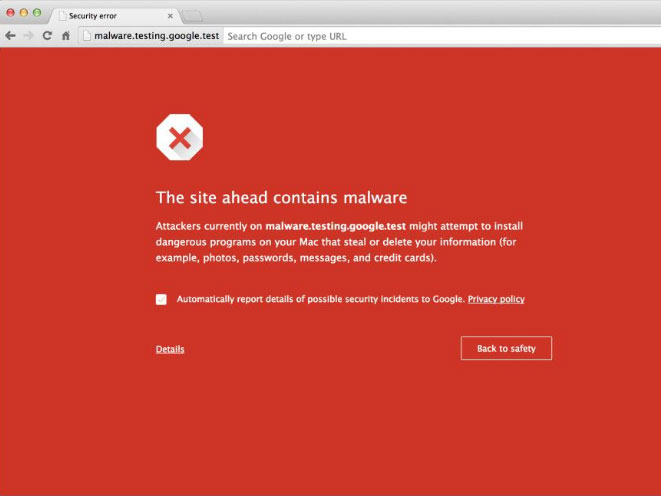
Hackers are always looking for ways to sneak malicious files onto other people’s websites. Recently we discovered a new technique they are using – actually, Google’s Webmaster tools detected it on a new client's website and warned about a Malware issue.
For the SEO-conscious folks out there, if Google flags your site for Malware, then anyone using Google Chrome will get a big red warning screen before entering your website. And you can watch your search ranking drop as well.
This Malware Injection method targets the File Upload fields created with the popular Webform module. If you are using a Webform file upload field, then your site could be vulnerable.
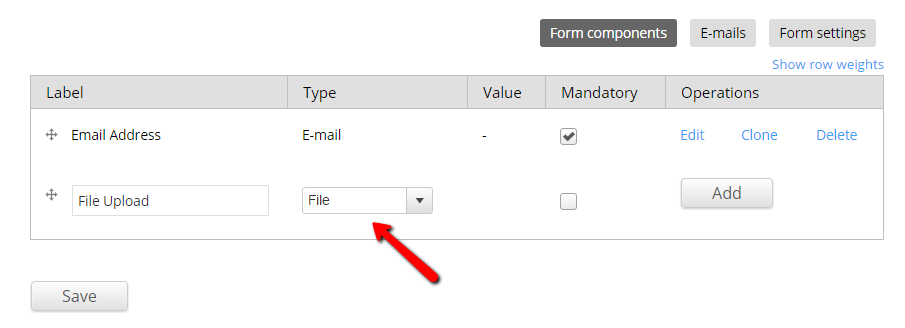
They are taking advantage of the File Webform component's Upload button that, via AJAX, allows the user to upload a file before submitting the form. That's right, they can upload a file to your server WITHOUT even submitting the form. Upon clicking the Upload button, the website default ajax functionality then displays the stored location of the file in plain sight almost instantly. So the attacker, can easily get the file loaded on your server, get the URL to it, with no possible form validation to stop them. This can get ugly.
If your File Upload allows PDF, they can then upload an innocent-looking PDF file... containing malware scripts. Yes, PDFs can contain malware because they have the capability of embedding Javascript code and executing files. Ref: http://security.stackexchange.com/questions/64052/can-a-pdf-file-contain-a-virus
Once they have this file on your website, they can send its direct link out to thousands of people. Also, if your website has high authority, they can also get the PDF ranking in Google to get people to click on it.
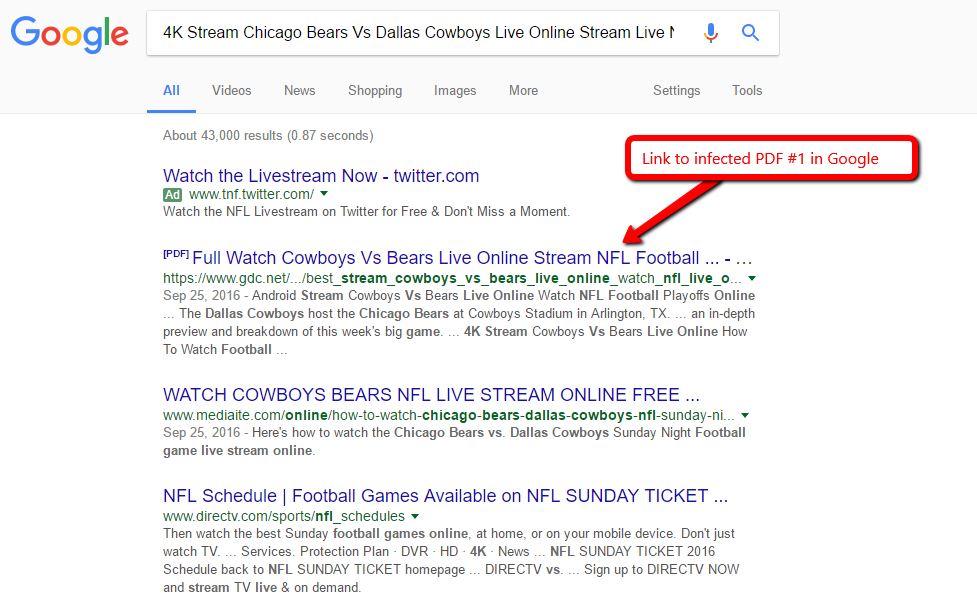
Here’s an example URL of a PDF file upload through a Webform:
http://[...]/sites/default/files/webform/4K_Stream_Chicago_Bears_Dallas_Cowboys_Live_Online_Stream_NFL_Football_Games.pdf
In this case, anyone searching for “4K Stream Chicago Bears Vs Dallas Cowboys Live Online Stream Live NFL Football Games”, could land on this Malware PDF served by your website! As was the case for this DA55 Drupal site. It looks like they deleted the file, but Google still has it indexed.
Any Webform that allows people to upload PDFs is a potential target. The most popular use-case I can think of is if you have Jobs section on your website and you allow people to upload their resumes, PDFs are generally permitted here. I've also seen some webforms allow HTML uploads, which are also being spammed.
Defending against it is pretty easy.
1. Patch your webform module. There is a patch to remove the ajax Upload button here: https://www.drupal.org/node/2820582#comment-11739661 - This will prevent the instant upload of files to your server.
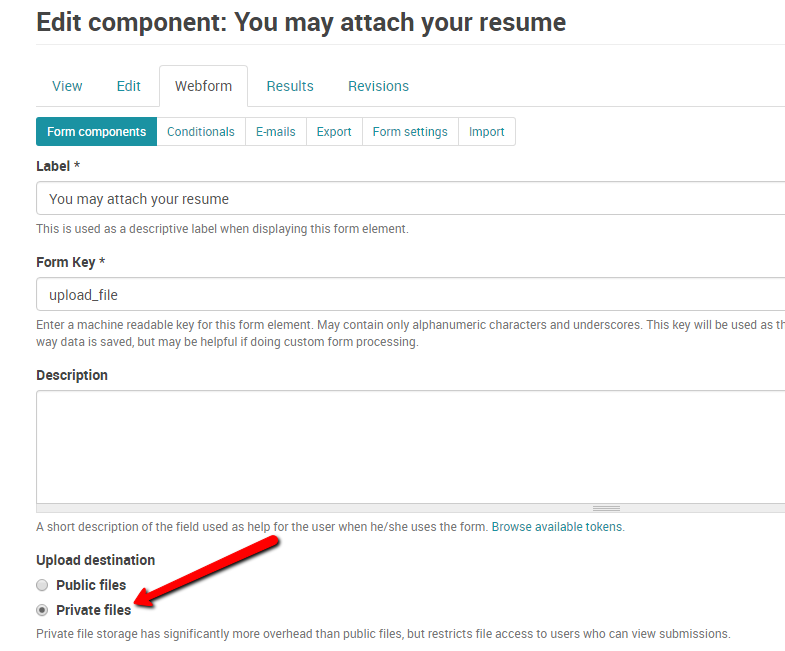
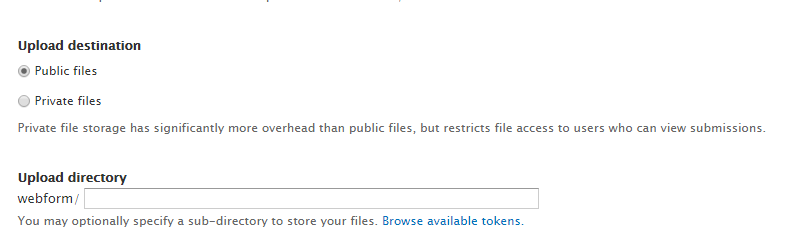
2. Be sure to set a custom path for your file uploads. Anything other than leaving it blank will work. This will help prevent the attacker from guessing the upload path upon submitting the form. You can also set your Upload destination to private, but that will prevent people receiving the link via email from opening a legitimate file without being logged into the site first - could be annoying to them.
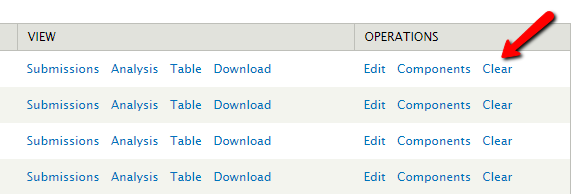
3. Clear out any old Webform submissions (http://[yoursite]/admin/content/webform)
4. Delete all Webform Upload files. If you were victim to this type of attack, then you should delete all the files in your webform upload directories. Like [sites/default/files/webform/] and any other custom paths you already set up. Remember the un-patched exposes the file's path, even your custom ones, so you need to clear them all.
5. Add anti-spam/anti-bot protection to your forms. This will prevent them from being uploaded if they are Bot submissions. We have an anti-spam article if you want more information about that.
6. Add a virus scanner to scan file uploads. If you have a server with ClamAV installed, you can install the ClamAV module which will scan incoming uploads. This module will verify that files uploaded to a site are not infected with a virus and prevent infected files from being saved. Just note that this only works with known/identified viruses and malware. I tested ClamAV against a bunch of these "4K" PDFs as mentioned above and they don't get identified as a virus or malware, perhaps they are just spam, but regardless Google identifies them as Malware.
Bob Kruse is the founder of Drupal Aid and a Drupal fanatic since 2008. He is also the creator of Cart Craze, an ecommerce website design gallery and Sick Journal, an online tool for keeping track of your family's health, sicknesses, and medications.
Each week we send 1 email to smart Drupal website owners. Enter your email below to receive our updates.
We will not share your email. 100% Privacy